Category Archives: Tutorials

WSL2 for pentesting – My experience
Hello all! I think it has been one month since I started using WSL2 for my CTF activities, and I have tested it in different environments. With this article I want to share my experience, hoping it will be useful to you, the reader. WSL2 Overview For those who don’t know WSL2, it’s the second…

OSINT & CLOSINT: Key Steps for Effective Threat Intelligence
In today’s cybersecurity landscape, gathering accurate and timely intelligence is critical for protecting both individuals and organizations. Two primary methodologies often used in this process are OSINT (Open Source Intelligence) and CLOSINT (Closed Source Intelligence). While OSINT focuses on freely accessible public data, CLOSINT dives into restricted, subscription-based, or underground sources for more specialized insight….

CPTS – My Preparation, Tips, and Advice
Introduction What is the CPTS? The Certified Penetration Testing Specialist (CPTS) is a highly regarded cybersecurity certification offered by Hack The Box (HTB). It is designed for professionals who want to validate their skills in ethical hacking and penetration testing. The CPTS certification demonstrates a candidate’s ability to conduct real-world security assessments, exploit vulnerabilities, and…
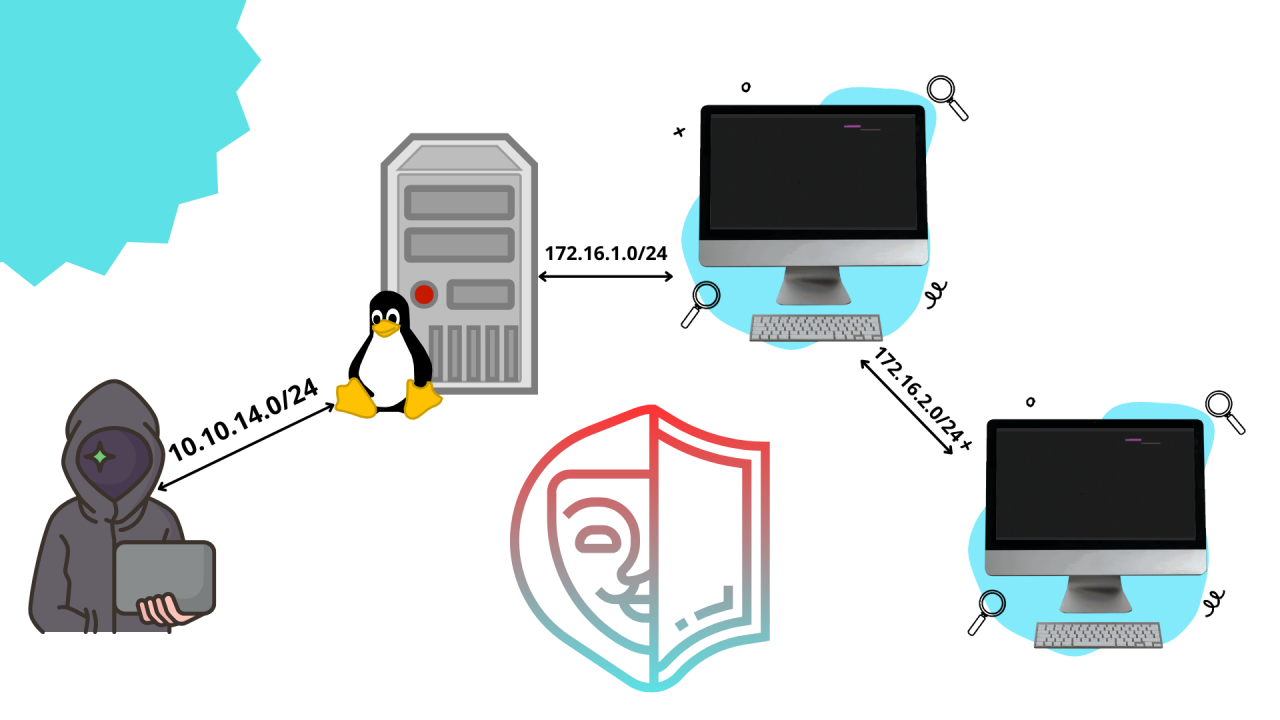
Ligolo-ng usage for pivoting
Description Are you tired to open tens of ports to reach a subnet? Or maybe you would like to reach a target as you were in his same network. In this article I’ll illustrate you an easy and efficient way to pivot through a network. What is pivoting? Pivoting is the ability of a threat actor…